Security: Difference between revisions
No edit summary |
|||
| (11 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
=== DOD TCSEC Rainbow Series === | |||
[[File: | https://en.wikipedia.org/wiki/Rainbow_Series | ||
The Red Book was initially published as the Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria, it was to provide additional information to the Orange Book principles in a network environment. | |||
[[File:NIST CSF2.png|thumb]] | |||
[[File:Itil4.png|thumb]] | [[File:Itil4.png|thumb]] | ||
| Line 12: | Line 14: | ||
=== OECD === | === OECD === | ||
1992: OECD: Guidelines for the Security of Information Systems | 1992: OECD: Guidelines for the Security of Information Systems | ||
2002: ... Towards a culture of security | |||
2002: [https://www.oecd-ilibrary.org/docserver/9789264059177-en-fr.pdf?expires=1721039454&id=id&accname=guest&checksum=B3680D5ADAE5F0D306F8EBFF66EEC418 ... Towards a culture of security] | |||
The objective of security of information systems is the protection of the interests of those relying on information systems from harm resulting from failures of availability, confidentiality, and integrity. | The objective of security of information systems is the protection of the interests of those relying on information systems from harm resulting from failures of availability, confidentiality, and integrity. | ||
Assets, Threats, Risks | |||
Common Criteria model | |||
BSIMM Maturity | |||
IEC 62443 SL ML | |||
ISO 27005 | |||
ISO 32000 | |||
=== Vulnerabilities === | === Vulnerabilities === | ||
| Line 29: | Line 44: | ||
https://attack.mitre.org/ | https://attack.mitre.org/ | ||
Conti, Cobaltstrike, Trickbot, Emotet, Lockbit, REvil, Hive, DarkSide | |||
Conti, Cobaltstrike, Trickbot, Emotet, Lockbit | |||
Sept 2020: Take down of Trickbot botnet | Sept 2020: Take down of Trickbot botnet | ||
Jan 2021: Take down of Emotet | Jan 2021: Take down of Emotet | ||
| Line 55: | Line 68: | ||
PsExec, Rclone | PsExec, Rclone | ||
=== Stack Overflow === | |||
https://insecure.org/stf/smashstack.html | |||
=== | |||
=== NIST SP 800-53 === | === NIST SP 800-53 === | ||
| Line 71: | Line 75: | ||
=== NIST CSF === | === NIST CSF === | ||
https://www.nist.gov/cyberframework | https://www.nist.gov/cyberframework | ||
[[File:CSF2.png|thumb]] | |||
https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf | |||
{| | {| | ||
|''' | |'''Governance''' | ||
|GV.OC | |||
|Organizational Context | |||
|- | |||
| | |||
|GV.RM | |||
|Risk Management Strategy | |||
|- | |||
| | | | ||
|GV.RR | |||
|Roles, Responsibilities and Authorities | |||
|- | |- | ||
| | | | ||
|GV.PO | |||
|Policy | |||
|- | |- | ||
| | | | ||
|GV.OV | |||
|Oversight | |||
|- | |- | ||
|GV| | | | ||
|GV.SC | |||
|Cybersecurity Supply Chain Risk Management | |||
|- | |- | ||
| | |'''Identify''' | ||
|ID.AM||Asset Management | |||
|- | |- | ||
| | | | ||
|ID.RA||Risk Assessment | |||
|- | |- | ||
| | | | ||
|ID.IM||Improvement | |||
|- | |- | ||
|'''Protect''' | |'''Protect''' | ||
|PR.AC||Identity Management and Access Control | |||
|- | |- | ||
| | | | ||
|PR.AT||Awareness and Training | |||
|- | |- | ||
| | | | ||
|PR.DS||Data Security | |||
|- | |- | ||
| | | | ||
|PR.PS||Platform Security | |||
|- | |- | ||
| | | | ||
|PR.IR||Technology Infrastructure Resilience | |||
| | |||
|- | |- | ||
|'''Detect''' | |'''Detect''' | ||
|DE.CM||Continuous Monitoring | |||
|- | |- | ||
| | | | ||
| | |DE.AE||Adverse Event Analysis | ||
|- | |- | ||
|'''Respond''' | |'''Respond''' | ||
|RS.MA||Incident Management | |||
|- | |- | ||
| | | | ||
|RS.CO||Incident Response Reporting and Communications | |||
|- | |- | ||
| | | | ||
|RS.AN||Incident Analysis | |||
|- | |- | ||
| | | | ||
|RS.IM||Incident Mitigation | |||
|- | |- | ||
| | |'''Recover''' | ||
|RC.RP||Incident Recovery Plan Execution | |||
|- | |- | ||
| | | | ||
| | |RC.CO||Incident Recovery Communication | ||
|} | |} | ||
| Line 1,804: | Line 1,821: | ||
|Perform Periodic Internal Penetration Tests | |Perform Periodic Internal Penetration Tests | ||
|} | |} | ||
https://github.com/bgpkit/monocle | |||
https://github.com/jcldf/ultimate-hardware-hacking-gear-guide- | |||
=== Privacy === | === Privacy === | ||
GDPR | |||
https://eur-lex.europa.eu/eli/reg/2016/679/oj | https://eur-lex.europa.eu/eli/reg/2016/679/oj | ||
| Line 1,823: | Line 1,846: | ||
20: Right to data portability | 20: Right to data portability | ||
https://www.enforcementtracker.com/ | https://www.enforcementtracker.com/ | ||
Latest revision as of 18:13, 16 July 2024
DOD TCSEC Rainbow Series
https://en.wikipedia.org/wiki/Rainbow_Series
The Red Book was initially published as the Trusted Network Interpretation of the Trusted Computer System Evaluation Criteria, it was to provide additional information to the Orange Book principles in a network environment.
OECD
1992: OECD: Guidelines for the Security of Information Systems
2002: ... Towards a culture of security
The objective of security of information systems is the protection of the interests of those relying on information systems from harm resulting from failures of availability, confidentiality, and integrity.
Assets, Threats, Risks
Common Criteria model
BSIMM Maturity
IEC 62443 SL ML
ISO 27005
ISO 32000
Vulnerabilities
https://nvd.nist.gov/vuln/search
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
Malware groups
Conti, Cobaltstrike, Trickbot, Emotet, Lockbit, REvil, Hive, DarkSide
Sept 2020: Take down of Trickbot botnet Jan 2021: Take down of Emotet Feb 2022: ContiLeaks (source, chat logs)
https://www.cisa.gov/uscert/ncas/alerts/aa21-265a
https://www.coveware.com/conti-ransomware
https://cyberint.com/blog/research/contileaks/
https://blog.malwarebytes.com/threat-intelligence/2022/03/the-conti-ransomware-leaks/
https://krebsonsecurity.com/2022/03/conti-ransomware-group-diaries-part-i-evasion/
https://threatpost.com/conti-ransomware-v-3-including-decryptor-leaked/179006/
Microsoft Windows Server Message Block 1.0 server vulnerabilities;
CVE-2021-34527 PrintNightmare vulnerability in Windows Print spooler service CVE-2020-1472 Zerologon vulnerability in Microsoft Active Directory Domain Controller systems.
PsExec, Rclone
Stack Overflow
https://insecure.org/stf/smashstack.html
NIST SP 800-53
https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
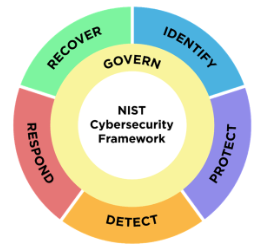
NIST CSF
https://www.nist.gov/cyberframework
https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf
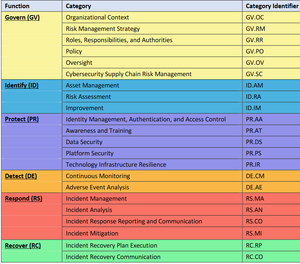
| Governance | GV.OC | Organizational Context |
| GV.RM | Risk Management Strategy | |
| GV.RR | Roles, Responsibilities and Authorities | |
| GV.PO | Policy | |
| GV.OV | Oversight | |
| GV.SC | Cybersecurity Supply Chain Risk Management | |
| Identify | ID.AM | Asset Management |
| ID.RA | Risk Assessment | |
| ID.IM | Improvement | |
| Protect | PR.AC | Identity Management and Access Control |
| PR.AT | Awareness and Training | |
| PR.DS | Data Security | |
| PR.PS | Platform Security | |
| PR.IR | Technology Infrastructure Resilience | |
| Detect | DE.CM | Continuous Monitoring |
| DE.AE | Adverse Event Analysis | |
| Respond | RS.MA | Incident Management |
| RS.CO | Incident Response Reporting and Communications | |
| RS.AN | Incident Analysis | |
| RS.IM | Incident Mitigation | |
| Recover | RC.RP | Incident Recovery Plan Execution |
| RC.CO | Incident Recovery Communication |
ISO 27002:2022
| control identifier | control name | type | property | concept | ||
| Organizational | 5.1 | Policies for information security | preventive | identify | ||
| 5.2 | Information security roles and responsibilities | preventive | identify | |||
| 5.3 | Segregation of duties | preventive | protect | |||
| 5.4 | Management responsibilities | preventive | identify | |||
| 5.5 | Contact with authorities | preventive,corrective | identify,protect,respond,recover | |||
| 5.6 | Contact with special interest groups | preventive,corrective | protect,respond,recover | |||
| 5.7 | Threat intelligence | preventive,detective,corrective | identify,detect,respond | |||
| 5.8 | Information security in project management | preventive | identify,protect | |||
| 5.9 | assets | Inventory of information and other associated assets | preventive | identify | ||
| 5.10 | Acceptable use of information and other associated assets | preventive | protect | |||
| 5.11 | Return of assets | preventive | protect | |||
| 5.12 | Classification of information | preventive | identify | |||
| 5.13 | Labelling of information | preventive | protect | |||
| 5.14 | Information transfer | preventive | protect | |||
| 5.15 | identity | Access control | preventive | protect | ||
| 5.16 | Identity management | preventive | protect | |||
| 5.17 | Authentication information | preventive | protect | |||
| 5.18 | Access rights | preventive | protect | |||
| 5.19 | Information security in supplier relationships | preventive | identify | |||
| 5.20 | Addressing information security within supplier agreements | preventive | identify | |||
| 5.21 | Managing information security in the ICT supply chain | preventive | identify | |||
| 5.22 | Monitoring, review and change management of supplier services | preventive | identify | |||
| 5.23 | Information security for use of cloud services | preventive | protect | |||
| 5.24 | incident | Information security incident management planning and preparation | corrective | respond,recover | ||
| 5.25 | Assessment and decision on information security events | preventive | detect,respond | |||
| 5.26 | Response to information security incidents | corrective | respond,recover | |||
| 5.27 | Learning from information security incidents | preventive | identify,protect | |||
| 5.28 | Collection of evidence | corrective | detect,respond | |||
| 5.29 | Information security during disruption | preventive,corrective | protect,respond | |||
| 5.30 | ICT readiness for business continuity | corrective | respond | |||
| 5.31 | Legal, statutory, regulatory and contractual requirements | preventive | identify | |||
| 5.32 | Intellectual property rights | preventive | identify | |||
| 5.33 | Protection of records | preventive | identify,protect | |||
| 5.34 | Privacy and protection of PII | preventive | identify,protect | |||
| 5.35 | Independent review of information security | preventive,corrective | identify,protect | |||
| 5.36 | Compliance with policies, rules and standards for information security | preventive | identify,protect | |||
| 5.37 | Documented operating procedures | preventive,corrective | protect,recover | |||
| People | 6.1 | Screening | preventive | protect | ||
| 6.2 | Terms and conditions of employment | preventive | protect | |||
| 6.3 | Information security awareness, education and training | preventive | protect | |||
| 6.4 | Disciplinary process | preventive,corrective | protect,respond | |||
| 6.5 | Responsibilities after termination or change of employment | preventive | protect | |||
| 6.6 | Confidentiality or non-disclosure agreements | preventive | protect | |||
| 6.7 | Remote working | preventive | protect | |||
| 6.8 | Information security event reporting | detective | detect | |||
| Physical | 7.1 | Physical security perimeters | preventive | protect | ||
| 7.2 | Physical entry | preventive | protect | |||
| 7.3 | Securing offices, rooms and facilities | preventive | protect | |||
| 7.4 | Physical security monitoring | preventive,detective | protect,detect | |||
| 7.5 | Protecting against physical and environmental threats | preventive | protect | |||
| 7.6 | Working in secure areas | preventive | protect | |||
| 7.7 | Clear desk and clear screen | preventive | protect | |||
| 7.8 | Equipment siting and protection | preventive | protect | |||
| 7.9 | Security of assets off-premises | preventive | protect | |||
| 7.10 | Storage media | preventive | protect | |||
| 7.11 | Supporting utilities | preventive,detective | protect,detect | |||
| 7.12 | Cabling security | preventive | protect | |||
| 7.13 | Equipment maintenance | preventive | protect | |||
| 7.14 | Secure disposal or re-use of equipment | preventive | protect | |||
| Technological | 8.1 | User endpoint devices | preventive | protect | ||
| 8.2 | Privileged access rights | preventive | protect | |||
| 8.3 | Information access restriction | preventive | protect | |||
| 8.4 | Access to source code | preventive | protect | |||
| 8.5 | Secure authentication | preventive | protect | |||
| 8.6 | Capacity management | preventive,detective | identify,protect,detect | |||
| 8.7 | Protection against malware | preventive,detective,corrective | protect,detect | |||
| 8.8 | Management of technical vulnerabilities | preventive | protect | |||
| 8.9 | Configuration management | preventive | protect | |||
| 8.10 | Information deletion | preventive | protect | |||
| 8.11 | Data masking | preventive | protect | |||
| 8.12 | Data leakage prevention | preventive | protect,detect | |||
| 8.13 | Information backup | corrective | protect | |||
| 8.14 | Redundancy of information processing facilities | preventive | protect | |||
| 8.15 | monitoring | Logging | preventive | protect | ||
| 8.16 | Monitoring activities | detective,corrective | detect,respond | |||
| 8.17 | Clock synchronization | preventive | protect,detect | |||
| 8.18 | Use of privileged utility programs | preventive | protect | |||
| 8.19 | Installation of software on operational systems | preventive | protect | |||
| 8.20 | hardening | Networks security | preventive,detective | protect,detect | ||
| 8.21 | Security of network services | preventive | protect | |||
| 8.22 | Segregation of networks | preventive | protect | |||
| 8.23 | Web filtering | preventive | protect | |||
| 8.24 | Use of cryptography | preventive | protect | |||
| 8.25 | Secure development life cycle | preventive | protect | |||
| 8.26 | Application security requirements | preventive | identify | |||
| 8.27 | Secure system architecture and engineering principles | preventive | protect | |||
| 8.28 | Secure coding | preventive | protect | |||
| 8.29 | Security testing in development and acceptance | preventive | identify | |||
| 8.30 | Outsourced development | preventive,detective | identify,protect,detect | |||
| 8.31 | Separation of development, test and production environments | preventive | protect | |||
| 8.32 | Change management | preventive | protect | |||
| 8.33 | Test information | preventive | protect | |||
| 8.34 | Protection of information systems during audit testing | preventive | protect | |||
CIS Controls (v8)
https://www.cisecurity.org/wp-content/uploads/2017/03/Poster_Winter2016_CSCs.pdf
| CIS Control | CIS Safeguard | Asset Type | Security Function | Title |
| 1 | Inventory and Control of Enterprise Assets | |||
| 1 | 1,1 | Devices | Identify | Establish and Maintain Detailed Enterprise Asset Inventory |
| 1 | 1,2 | Devices | Respond | Address Unauthorized Assets |
| 1 | 1,3 | Devices | Detect | Utilize an Active Discovery Tool |
| 1 | 1,4 | Devices | Identify | Use Dynamic Host Configuration Protocol (DHCP) Logging to Update Enterprise Asset Inventory |
| 1 | 1,5 | Devices | Detect | Use a Passive Asset Discovery Tool |
| 2 | Inventory and Control of Software Assets | |||
| 2 | 2,1 | Applications | Identify | Establish and Maintain a Software Inventory |
| 2 | 2,2 | Applications | Identify | Ensure Authorized Software is Currently Supported |
| 2 | 2,3 | Applications | Respond | Address Unauthorized Software |
| 2 | 2,4 | Applications | Detect | Utilize Automated Software Inventory Tools |
| 2 | 2,5 | Applications | Protect | Allowlist Authorized Software |
| 2 | 2,6 | Applications | Protect | Allowlist Authorized Libraries |
| 2 | 2,7 | Applications | Protect | Allowlist Authorized Scripts |
| 3 | Data Protection | |||
| 3 | 3,1 | Data | Identify | Establish and Maintain a Data Management Process |
| 3 | 3,2 | Data | Identify | Establish and Maintain a Data Inventory |
| 3 | 3,3 | Data | Protect | Configure Data Access Control Lists |
| 3 | 3,4 | Data | Protect | Enforce Data Retention |
| 3 | 3,5 | Data | Protect | Securely Dispose of Data |
| 3 | 3,6 | Devices | Protect | Encrypt Data on End-User Devices |
| 3 | 3,7 | Data | Identify | Establish and Maintain a Data Classification Scheme |
| 3 | 3,8 | Data | Identify | Document Data Flows |
| 3 | 3,9 | Data | Protect | Encrypt Data on Removable Media |
| 3 | 3,10 | Data | Protect | Encrypt Sensitive Data in Transit |
| 3 | 3,11 | Data | Protect | Encrypt Sensitive Data at Rest |
| 3 | 3,12 | Network | Protect | Segment Data Processing and Storage Based on Sensitivity |
| 3 | 3,13 | Data | Protect | Deploy a Data Loss Prevention Solution |
| 3 | 3,14 | Data | Detect | Log Sensitive Data Access |
| 4 | Secure Configuration of Enterprise Assets and Software | |||
| 4 | 4,1 | Applications | Protect | Establish and Maintain a Secure Configuration Process |
| 4 | 4,2 | Network | Protect | Establish and Maintain a Secure Configuration Process for Network Infrastructure |
| 4 | 4,3 | Users | Protect | Configure Automatic Session Locking on Enterprise Assets |
| 4 | 4,4 | Devices | Protect | Implement and Manage a Firewall on Servers |
| 4 | 4,5 | Devices | Protect | Implement and Manage a Firewall on End-User Devices |
| 4 | 4,6 | Network | Protect | Securely Manage Enterprise Assets and Software |
| 4 | 4,7 | Users | Protect | Manage Default Accounts on Enterprise Assets and Software |
| 4 | 4,8 | Devices | Protect | Uninstall or Disable Unnecessary Services on Enterprise Assets and Software |
| 4 | 4,9 | Devices | Protect | Configure Trusted DNS Servers on Enterprise Assets |
| 4 | 4,10 | Devices | Respond | Enforce Automatic Device Lockout on Portable End-User Devices |
| 4 | 4,11 | Devices | Protect | Enforce Remote Wipe Capability on Portable End-User Devices |
| 4 | 4,12 | Devices | Protect | Separate Enterprise Workspaces on Mobile End-User Devices |
| 5 | Account Management | |||
| 5 | 5,1 | Users | Identify | Establish and Maintain an Inventory of Accounts |
| 5 | 5,2 | Users | Protect | Use Unique Passwords |
| 5 | 5,3 | Users | Respond | Disable Dormant Accounts |
| 5 | 5,4 | Users | Protect | Restrict Administrator Privileges to Dedicated Administrator Accounts |
| 5 | 5,5 | Users | Identify | Establish and Maintain an Inventory of Service Accounts |
| 5 | 5,6 | Users | Protect | Centralize Account Management |
| 6 | Access Control Management | |||
| 6 | 6,1 | Users | Protect | Establish an Access Granting Process |
| 6 | 6,2 | Users | Protect | Establish an Access Revoking Process |
| 6 | 6,3 | Users | Protect | Require MFA for Externally-Exposed Applications |
| 6 | 6,4 | Users | Protect | Require MFA for Remote Network Access |
| 6 | 6,5 | Users | Protect | Require MFA for Administrative Access |
| 6 | 6,6 | Users | Identify | Establish and Maintain an Inventory of Authentication and Authorization Systems |
| 6 | 6,7 | Users | Protect | Centralize Access Control |
| 6 | 6,8 | Data | Protect | Define and Maintain Role-Based Access Control |
| 7 | Continuous Vulnerability Management | |||
| 7 | 7,1 | Applications | Protect | Establish and Maintain a Vulnerability Management Process |
| 7 | 7,2 | Applications | Respond | Establish and Maintain a Remediation Process |
| 7 | 7,3 | Applications | Protect | Perform Automated Operating System Patch Management |
| 7 | 7,4 | Applications | Protect | Perform Automated Application Patch Management |
| 7 | 7,5 | Applications | Identify | Perform Automated Vulnerability Scans of Internal Enterprise Assets |
| 7 | 7,6 | Applications | Identify | Perform Automated Vulnerability Scans of Externally-Exposed Enterprise Assets |
| 7 | 7,7 | Applications | Respond | Remediate Detected Vulnerabilities |
| 8 | Audit Log Management | |||
| 8 | 8,1 | Network | Protect | Establish and Maintain an Audit Log Management Process |
| 8 | 8,2 | Network | Detect | Collect Audit Logs |
| 8 | 8,3 | Network | Protect | Ensure Adequate Audit Log Storage |
| 8 | 8,4 | Network | Protect | Standardize Time Synchronization |
| 8 | 8,5 | Network | Detect | Collect Detailed Audit Logs |
| 8 | 8,6 | Network | Detect | Collect DNS Query Audit Logs |
| 8 | 8,7 | Network | Detect | Collect URL Request Audit Logs |
| 8 | 8,8 | Devices | Detect | Collect Command-Line Audit Logs |
| 8 | 8,9 | Network | Detect | Centralize Audit Logs |
| 8 | 8,10 | Network | Protect | Retain Audit Logs |
| 8 | 8,11 | Network | Detect | Conduct Audit Log Reviews |
| 8 | 8,12 | Data | Detect | Collect Service Provider Logs |
| 9 | Email and Web Browser Protections | |||
| 9 | 9,1 | Applications | Protect | Ensure Use of Only Fully Supported Browsers and Email Clients |
| 9 | 9,2 | Network | Protect | Use DNS Filtering Services |
| 9 | 9,3 | Network | Protect | Maintain and Enforce Network-Based URL Filters |
| 9 | 9,4 | Applications | Protect | Restrict Unnecessary or Unauthorized Browser and Email Client Extensions |
| 9 | 9,5 | Network | Protect | Implement DMARC |
| 9 | 9,6 | Network | Protect | Block Unnecessary File Types |
| 9 | 9,7 | Network | Protect | Deploy and Maintain Email Server Anti-Malware Protections |
| 10 | Malware Defenses | |||
| 10 | 10,1 | Devices | Protect | Deploy and Maintain Anti-Malware Software |
| 10 | 10,2 | Devices | Protect | Configure Automatic Anti-Malware Signature Updates |
| 10 | 10,3 | Devices | Protect | Disable Autorun and Autoplay for Removable Media |
| 10 | 10,4 | Devices | Detect | Configure Automatic Anti-Malware Scanning of Removable Media |
| 10 | 10,5 | Devices | Protect | Enable Anti-Exploitation Features |
| 10 | 10,6 | Devices | Protect | Centrally Manage Anti-Malware Software |
| 10 | 10,7 | Devices | Detect | Use Behavior-Based Anti-Malware Software |
| 11 | Data Recovery | |||
| 11 | 11,1 | Data | Recover | Establish and Maintain a Data Recovery Process |
| 11 | 11,2 | Data | Recover | Perform Automated Backups |
| 11 | 11,3 | Data | Protect | Protect Recovery Data |
| 11 | 11,4 | Data | Recover | Establish and Maintain an Isolated Instance of Recovery Data |
| 11 | 11,5 | Data | Recover | Test Data Recovery |
| 12 | Network Infrastructure Management | |||
| 12 | 12,1 | Network | Protect | Ensure Network Infrastructure is Up-to-Date |
| 12 | 12,2 | Network | Protect | Establish and Maintain a Secure Network Architecture |
| 12 | 12,3 | Network | Protect | Securely Manage Network Infrastructure |
| 12 | 12,4 | Network | Identify | Establish and Maintain Architecture Diagram(s) |
| 12 | 12,5 | Network | Protect | Centralize Network Authentication, Authorization, and Auditing (AAA) |
| 12 | 12,6 | Network | Protect | Use of Secure Network Management and Communication Protocols |
| 12 | 12,7 | Devices | Protect | Ensure Remote Devices Utilize a VPN and are Connecting to an Enterprise’s AAA Infrastructure |
| 12 | 12,8 | Devices | Protect | Establish and Maintain Dedicated Computing Resources for All Administrative Work |
| 13 | Network Monitoring and Defense | |||
| 13 | 13,1 | Network | Detect | Centralize Security Event Alerting |
| 13 | 13,2 | Devices | Detect | Deploy a Host-Based Intrusion Detection Solution |
| 13 | 13,3 | Network | Detect | Deploy a Network Intrusion Detection Solution |
| 13 | 13,4 | Network | Protect | Perform Traffic Filtering Between Network Segments |
| 13 | 13,5 | Devices | Protect | Manage Access Control for Remote Assets |
| 13 | 13,6 | Network | Detect | Collect Network Traffic Flow Logs |
| 13 | 13,7 | Devices | Protect | Deploy a Host-Based Intrusion Prevention Solution |
| 13 | 13,8 | Network | Protect | Deploy a Network Intrusion Prevention Solution |
| 13 | 13,9 | Devices | Protect | Deploy Port-Level Access Control |
| 13 | 13,10 | Network | Protect | Perform Application Layer Filtering |
| 13 | 13,11 | Network | Detect | Tune Security Event Alerting Thresholds |
| 14 | Security Awareness and Skills Training | |||
| 14 | 14,1 | N/A | Protect | Establish and Maintain a Security Awareness Program |
| 14 | 14,2 | N/A | Protect | Train Workforce Members to Recognize Social Engineering Attacks |
| 14 | 14,3 | N/A | Protect | Train Workforce Members on Authentication Best Practices |
| 14 | 14,4 | N/A | Protect | Train Workforce on Data Handling Best Practices |
| 14 | 14,5 | N/A | Protect | Train Workforce Members on Causes of Unintentional Data Exposure |
| 14 | 14,6 | N/A | Protect | Train Workforce Members on Recognizing and Reporting Security Incidents |
| 14 | 14,7 | N/A | Protect | Train Workforce on How to Identify and Report if Their Enterprise Assets are Missing Security Updates |
| 14 | 14,8 | N/A | Protect | Train Workforce on the Dangers of Connecting to and Transmitting Enterprise Data Over Insecure Networks |
| 14 | 14,9 | N/A | Protect | Conduct Role-Specific Security Awareness and Skills Training |
| 15 | Service Provider Management | |||
| 15 | 15,1 | N/A | Identify | Establish and Maintain an Inventory of Service Providers |
| 15 | 15,2 | N/A | Identify | Establish and Maintain a Service Provider Management Policy |
| 15 | 15,3 | N/A | Identify | Classify Service Providers |
| 15 | 15,4 | N/A | Protect | Ensure Service Provider Contracts Include Security Requirements |
| 15 | 15,5 | N/A | Identify | Assess Service Providers |
| 15 | 15,6 | Data | Detect | Monitor Service Providers |
| 15 | 15,7 | Data | Protect | Securely Decommission Service Providers |
| 16 | Application Software Security | |||
| 16 | 16,1 | Applications | Protect | Establish and Maintain a Secure Application Development Process |
| 16 | 16,2 | Applications | Protect | Establish and Maintain a Process to Accept and Address Software Vulnerabilities |
| 16 | 16,3 | Applications | Protect | Perform Root Cause Analysis on Security Vulnerabilities |
| 16 | 16,4 | Applications | Protect | Establish and Manage an Inventory of Third-Party Software Components |
| 16 | 16,5 | Applications | Protect | Use Up-to-Date and Trusted Third-Party Software Components |
| 16 | 16,6 | Applications | Protect | Establish and Maintain a Severity Rating System and Process for Application Vulnerabilities |
| 16 | 16,7 | Applications | Protect | Use Standard Hardening Configuration Templates for Application Infrastructure |
| 16 | 16,8 | Applications | Protect | Separate Production and Non-Production Systems |
| 16 | 16,9 | Applications | Protect | Train Developers in Application Security Concepts and Secure Coding |
| 16 | 16,10 | Applications | Protect | Apply Secure Design Principles in Application Architectures |
| 16 | 16,11 | Applications | Protect | Leverage Vetted Modules or Services for Application Security Components |
| 16 | 16,12 | Applications | Protect | Implement Code-Level Security Checks |
| 16 | 16,13 | Applications | Protect | Conduct Application Penetration Testing |
| 16 | 16,14 | Applications | Protect | Conduct Threat Modeling |
| 17 | Incident Response Management | |||
| 17 | 17,1 | N/A | Respond | Designate Personnel to Manage Incident Handling |
| 17 | 17,2 | N/A | Respond | Establish and Maintain Contact Information for Reporting Security Incidents |
| 17 | 17,3 | N/A | Respond | Establish and Maintain an Enterprise Process for Reporting Incidents |
| 17 | 17,4 | N/A | Respond | Establish and Maintain an Incident Response Process |
| 17 | 17,5 | N/A | Respond | Assign Key Roles and Responsibilities |
| 17 | 17,6 | N/A | Respond | Define Mechanisms for Communicating During Incident Response |
| 17 | 17,7 | N/A | Recover | Conduct Routine Incident Response Exercises |
| 17 | 17,8 | N/A | Recover | Conduct Post-Incident Reviews |
| 17 | 17,9 | N/A | Recover | Establish and Maintain Security Incident Thresholds |
| 18 | Penetration Testing | |||
| 18 | 18,1 | N/A | Identify | Establish and Maintain a Penetration Testing Program |
| 18 | 18,2 | Network | Identify | Perform Periodic External Penetration Tests |
| 18 | 18,3 | Network | Protect | Remediate Penetration Test Findings |
| 18 | 18,4 | Network | Protect | Validate Security Measures |
| 18 | 18,5 | N/A | Identify | Perform Periodic Internal Penetration Tests |
https://github.com/bgpkit/monocle
https://github.com/jcldf/ultimate-hardware-hacking-gear-guide-
Privacy
GDPR
https://eur-lex.europa.eu/eli/reg/2016/679/oj
Lawfulness, Fairness, and Transparency; Purpose Limitation; Data Minimisation; Accuracy; Storage Limitations; Integrity and Confidentiality; and Accountability.
Chapter 3: Rights of the data subject
15: Right of access by the data subject
16: Right to rectification
17: Right to erasure
18: Right to restriction of processing
19: Notification obligation regarding rectification or erasure of personal data or restriction of processing
20: Right to data portability